Drone sightings around the world are rapidly increasing, prompting significant concerns regarding security, privacy, and airspace management. This global phenomenon necessitates a comprehensive analysis of the geographic distribution of sightings, the types of drones involved, the motivations behind their operation, responses from authorities, relevant legal frameworks, and the overall societal impact. This report aims to provide a data-driven overview of this complex issue.
The proliferation of unmanned aerial vehicles (UAVs), commonly known as drones, has created both opportunities and challenges across various sectors. From agricultural applications and infrastructure monitoring to potential misuse for illicit activities, the diverse functionalities of drones necessitate a multifaceted approach to understanding their impact. This study will examine the diverse range of drone types, operational motivations, and regulatory responses implemented globally.
Types of Drones Involved in Sightings

Unidentified aerial phenomena (UAP) reports frequently involve drones, necessitating a detailed understanding of the various types and their capabilities to effectively analyze sightings. Distinguishing between civilian, military, and illicitly used drones is crucial for accurate assessment and appropriate response. This analysis focuses on the common types of drones observed globally, their specifications, and potential applications.
The diversity of drones observed in reported sightings reflects both technological advancements and the varied purposes for which they are deployed. Size, purpose, and technology employed are key factors differentiating these unmanned aerial vehicles (UAVs).
Increased global drone sightings necessitate a standardized regulatory framework. The rise in unauthorized drone operations highlights the importance of responsible drone operation, prompting many countries to implement licensing systems. To operate legally in Canada, obtaining a drone licence is mandatory, as detailed on the official resource drone licence canada website. This licensing process aims to mitigate the risks associated with the increasing number of drone sightings worldwide.
Drone Categorization by Size, Purpose, and Technology
The following categorization provides a framework for understanding the types of drones involved in reported sightings. The specifications and capabilities listed are representative and may vary depending on the specific model and manufacturer.
- Small Drones (Micro and Mini): Typically weighing less than 2 kg, these drones are often used for recreational purposes, photography, and videography. They are characterized by their portability, ease of use, and relatively low cost. Specifications vary greatly, but common features include onboard cameras, GPS modules, and flight times ranging from 15 to 30 minutes. Military applications may involve reconnaissance or surveillance in limited contexts.
- Medium-Sized Drones: These drones, weighing between 2 kg and 25 kg, encompass a broad range of applications. Commercial uses include aerial surveying, infrastructure inspection, and delivery services. Their larger size allows for greater payload capacity and longer flight times, often exceeding an hour. More advanced features such as obstacle avoidance systems and advanced sensors are common. Military applications could include larger-scale surveillance or targeted payload delivery.
- Large Drones (Heavy-Lift): Weighing over 25 kg, these drones are capable of carrying significant payloads, making them suitable for tasks such as cargo transport, search and rescue operations, and precision agriculture. They often utilize more robust propulsion systems and sophisticated flight control systems. Military versions could be used for transporting equipment, deploying payloads, or conducting longer-range surveillance missions.
Comparison of Civilian and Military/Illicit Drones
While many drone designs are inherently dual-use, key differences exist between civilian and military/illicit drones, particularly regarding their capabilities and intended purposes. These distinctions are crucial for analyzing UAP reports.
Reports of unauthorized drone activity are increasing globally, posing challenges to airspace safety and security. A comprehensive understanding of these incidents requires data aggregation, such as that provided by resources like drone sightings around the world , which can help researchers analyze trends and patterns in geographical distribution and operational characteristics of these sightings. Such analyses are crucial for developing effective countermeasures and regulatory frameworks.
| Feature | Civilian Drones | Military/Illicit Drones |
|---|---|---|
| Payload Capacity | Typically limited to cameras, sensors, or small packages | Can carry weapons, surveillance equipment, or other specialized payloads |
| Flight Range | Generally limited to a few kilometers | Can have significantly extended ranges, often exceeding 100 kilometers |
| Stealth Capabilities | Minimal or absent | May incorporate features designed to reduce detectability, such as low radar signatures |
| Communication Systems | Typically rely on standard radio frequencies | May utilize encrypted or secure communication channels |
| Flight Autonomy | Often rely on GPS and pre-programmed flight paths | May incorporate advanced AI and autonomous flight capabilities |
Motivations Behind Drone Sightings: Drone Sightings Around The World
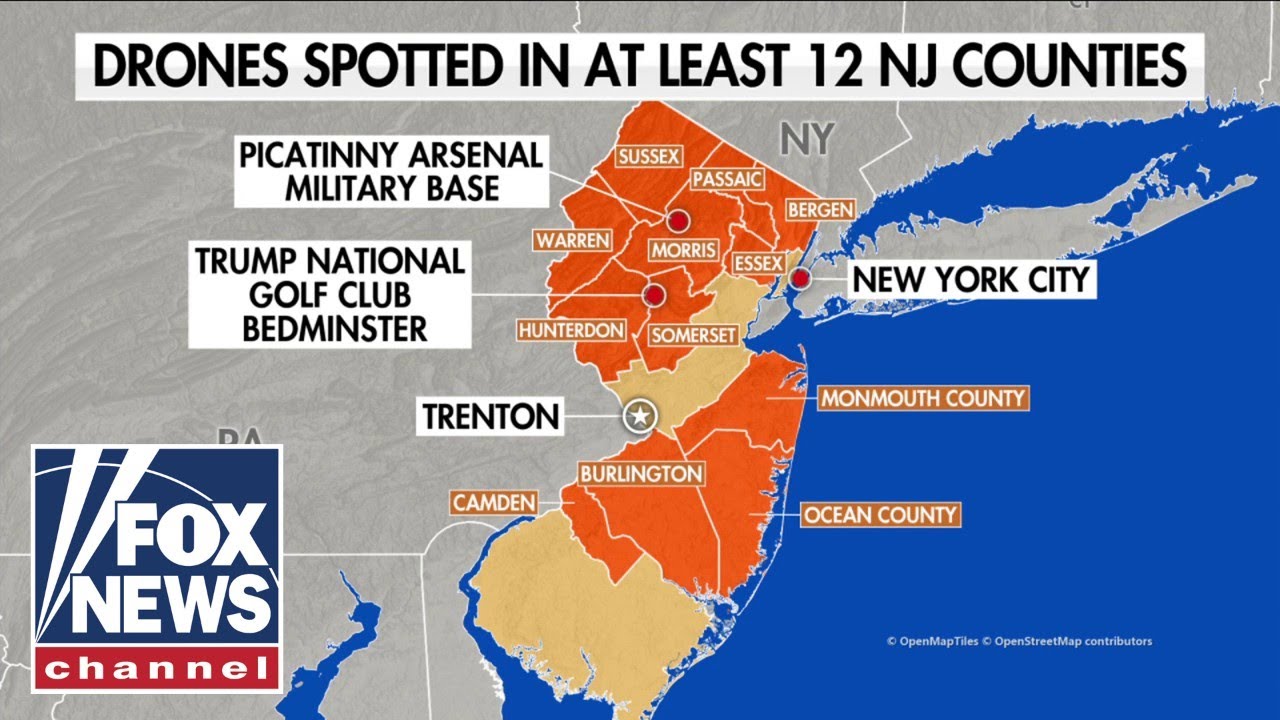
Drone sightings, whether reported by civilians or detected by air traffic control systems, stem from a diverse range of motivations. Understanding these motivations is crucial for developing effective countermeasures and mitigating potential risks. These motivations can be broadly categorized as legitimate, often involving commercial or research applications, and potentially malicious, encompassing activities that threaten safety and security.The operational context significantly influences the purpose of a drone flight.
Legitimate uses often adhere to regulations and involve prior authorization, while malicious operations are typically clandestine and aim to circumvent oversight. Distinguishing between these categories requires careful analysis of the operational circumstances, including the drone’s flight path, altitude, and payload.
Legitimate Drone Operations
Legitimate drone operations encompass a wide spectrum of activities across various sectors. These operations contribute significantly to economic productivity and scientific advancement, but require robust regulatory frameworks to ensure safety and prevent misuse.
- Agriculture: Drones equipped with multispectral or hyperspectral cameras are employed for precision agriculture, monitoring crop health, identifying areas requiring targeted treatment (e.g., fertilization or pesticide application), and optimizing irrigation strategies. This leads to increased yields and reduced resource consumption.
- Infrastructure Inspection: Drones provide a cost-effective and efficient method for inspecting bridges, power lines, pipelines, and other critical infrastructure. They can access hard-to-reach areas, reducing the need for expensive and potentially dangerous human intervention. High-resolution imagery and data collected by drones allow for early detection of structural defects and potential failures.
- Surveillance and Monitoring: Law enforcement agencies, search and rescue teams, and environmental monitoring organizations utilize drones for surveillance, tracking, and data acquisition. Examples include monitoring wildlife populations, assessing disaster damage, and tracking suspects in criminal investigations. This necessitates strict adherence to privacy regulations and ethical guidelines.
Potentially Malicious Drone Operations
Unauthorized drone operations pose significant security risks, particularly when conducted near critical infrastructure or restricted airspace. The potential for malicious use necessitates proactive measures to detect and mitigate such threats.
- Smuggling: Drones are increasingly used for smuggling illicit goods, such as drugs, weapons, and contraband, across borders or into secure facilities. Their maneuverability and capacity for autonomous flight make them a challenging target for conventional security measures.
- Terrorism and Espionage: The potential for drones to be weaponized or used for surveillance poses a serious threat to national security. Drones can be equipped with explosives or used to gather intelligence on critical infrastructure or military installations. This necessitates advanced detection and counter-drone technologies.
- Unauthorized Access to Restricted Airspace: Unauthorized drone flights near airports, government buildings, or other sensitive locations pose a significant safety risk. Collisions with aircraft or the potential for drones to be used to deliver harmful payloads necessitate robust airspace management and detection systems.
Security Risks Associated with Unauthorized Drone Operations
The unauthorized operation of drones near critical infrastructure or restricted airspace presents a multitude of security risks. These risks range from disruption of operations to potential catastrophic events.
Unauthorized drone operations near airports can lead to significant disruptions, including flight delays and potential collisions with aircraft, posing a serious threat to aviation safety. Similarly, the use of drones to deliver explosives or other harmful payloads to critical infrastructure could have devastating consequences.
Array
Unauthorized drone activity poses significant security and safety risks, necessitating robust detection and response mechanisms. Authorities worldwide employ a range of strategies to mitigate these threats, balancing the need for effective countermeasures with considerations of privacy and proportionality. The effectiveness of these methods varies depending on factors such as drone type, operating environment, and available technology.
Methods for Detecting and Responding to Unauthorized Drone Activity
Detection of unauthorized drones typically involves a multi-layered approach combining technological and human resources. Initial detection often relies on visual observation by trained personnel, supplemented by acoustic sensors that identify the characteristic sound of drone rotors. More sophisticated systems utilize radar technology to detect drones at greater distances and through various environmental conditions, even in challenging weather. Radio frequency (RF) detection systems pinpoint the drone’s radio signals, allowing for identification and tracking.
Furthermore, some systems leverage artificial intelligence (AI) to analyze sensor data, automatically classifying objects and triggering alerts when suspicious activity is detected. Response strategies range from issuing warnings to deploying counter-drone technologies, depending on the perceived threat level and the legal framework in place.
Effectiveness of Counter-Drone Technologies
Several counter-drone technologies are currently deployed or under development. Jamming technology disrupts the drone’s communication signals, rendering it unable to receive commands from its operator and potentially causing it to land. However, jamming can also interfere with other radio frequency devices, posing a potential risk to public safety and requiring careful consideration of frequency bands and geographical limitations.
Netting systems physically capture the drone, either by deploying a net from a remote location or by using a tethered net. This method is effective for smaller drones but can be less successful against larger or faster models. Directed energy weapons (DEWs), such as lasers, offer the potential for precise targeting and disabling of drones without causing physical damage to surrounding infrastructure or personnel.
However, the effectiveness of DEWs depends on factors such as weather conditions, distance, and the drone’s materials. The development and deployment of DEWs also raise ethical and legal considerations related to their potential for misuse.
Typical Response Protocol to a Drone Sighting, Drone sightings around the world
The response protocol to a drone sighting typically follows a structured process. A flowchart visually represents this process:[The following describes a flowchart. Due to the limitations of the HTML plaintext format, a visual representation cannot be directly provided. The flowchart would consist of boxes and arrows. ] Box 1: Initial Detection (Visual, Acoustic, Radar, RF)
This box represents the initial detection of a drone via any of the detection methods mentioned above.
Arrow 1: Suspicious Activity Identified?
This arrow points from Box 1 to Box 2 (Yes) and Box 3 (No).
Box 2: Confirmation and Assessment of Threat Level
This box involves verifying the drone’s unauthorized nature and assessing the potential risk it poses (e.g., location, proximity to critical infrastructure, suspected intent).
Arrow 2: Threat Level Requires Immediate Action?
This arrow points from Box 2 to Box 4 (Yes) and Box 5 (No).
Box 3: No Further Action Required
This box represents the conclusion of the process if the drone is deemed non-threatening.
Box 4: Deployment of Counter-Drone Technology (Jamming, Netting, DEWs)
This box represents the implementation of countermeasures, chosen based on the threat level and available resources.
Arrow 3: Drone Neutralized?
This arrow points from Box 4 to Box 6 (Yes) and Box 7 (No).
Box 5: Monitoring and Observation
This box represents the continued observation of the drone, awaiting further developments or escalating the response if necessary.
Box 6: Secure Drone and Investigate
This box represents the securing of the drone and the initiation of an investigation to determine the operator’s identity and motives.
Box 7: Escalate Response/Seek Additional Support
This box represents the need for a higher level of intervention, potentially involving law enforcement or specialized counter-drone units.
The increasing frequency of drone sightings globally underscores the need for robust international cooperation and standardized regulatory frameworks. While drone technology offers significant benefits across numerous sectors, addressing the security and privacy concerns associated with unauthorized drone operations remains crucial. Future research should focus on developing more effective counter-drone technologies and enhancing public awareness of responsible drone usage to mitigate potential risks and maximize the positive societal impacts of this transformative technology.
Frequently Asked Questions
What are the most common causes of accidental drone sightings?
Accidental sightings often result from pilot error, equipment malfunction, or unexpected weather conditions leading to drones drifting off course.
How are drone sightings impacting wildlife?
Studies are ongoing, but some evidence suggests potential impacts on wildlife behavior and breeding patterns due to noise and disturbance from drones.
What is the role of insurance in drone operations?
Drone operators are increasingly required to carry liability insurance to cover potential damages or injuries caused by their drones.
Are there international treaties governing drone usage in international airspace?
While no single, comprehensive treaty exists, various international agreements and conventions address aspects of airspace sovereignty and the safe operation of aircraft, including drones, in international airspace.